As Tax Week arrives, tax agencies may be overlooking fraud happening under their noses – fraud perpetrated by insider threats. While the agencies are focused on the hot fraud topics of the day – identity verification quizzing, protecting PIN files, and cybersecurity – insider threats pose a particularly insidious risk.
According to the CERT Division of the Carnegie Mellon Software Engineering Institute (SEI), insider threat is “the potential for an individual who has or had authorized access to an organization's assets to use their access, either maliciously or unintentionally, to act in a way that could negatively affect the organization.” If these opportunistic employees work for you, and they get caught, you will be held responsible for not having insight into their activities. While they may wind up in jail, you could wind up losing your career.
“But I have great employees”, you say. “They would never do that.” As it turns out, many insiders who steal or modify information are recruited by outsiders, including organized crime and foreign organizations. Even employees who have shown 20-years of unblemished, loyal performance can unfortunately fall prey to these outsiders at a time of financial strain or personal difficulty. Additionally, with increased use of private sector business partners, your organization is no longer your own. There has been an increased number of insider crimes committed by employees of trusted business partners (e.g. contractors, temp-workers) who have been given authorized access to their clients’ networks, systems and data.
Insiders have a significant advantage over external attackers. Insiders are aware of their organization’s policies, procedures, and technology: they are often also aware of their vulnerabilities, such as loosely enforced policies and procedures or exploitable technical flaws in networks or systems. To add salt to the wound, organizations tend to manage their responses to insider threats “in-house”. This may have the unintended result of hiding the insider threat problem at large. When the Washington, D.C. government suffered at the hands of an unethical employee several years ago, it went public (to the benefit of their peers who could extract the lessons learned) but many do not.
According to the SEI in their overview of their 2016 U.S. State of Cybercrime Survey:
- 47% of survey participants reported that an insider incident was committed against their organization.
- 27% of the attacks against their organization were committed by insiders
- The most common insider incidents were customer records compromised or stolen, confidential records (trade secrets or intellectual property) compromised or stolen, and private or sensitive information unintentionally exposed.
As someone in a leadership role in a tax agency, doing nothing can be a risky proposition (both operationally and politically). So, what can you do?
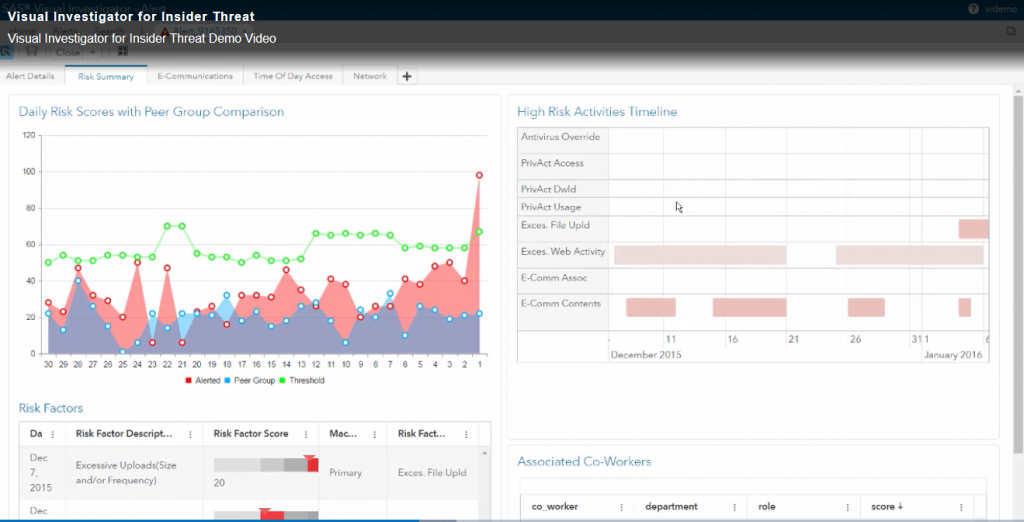
The first thing you can do is familiarize yourself with the “insider threat industry”. There are many resources including Carnegie Mellon’s CERT Division and industry white papers . Additionally, learn about the most modern insider-threat detection solutions, such as SAS Visual Investigator for Insider Threat, which find the threats for you while you’re busy working.
These systems can use data already at your disposal to identify:
- File downloads which are excessive for the employee’s peer group
- Atypical privileged account access (e.g. VIP taxpayers)
- Abnormal viewing/modification of taxpayer accounts
- Excessive web activity
- Sentiments (i.e. feelings) expressed in work email that are highly correlated with insider threat
- Unusual time-of-day access
- Employees’ connections and sphere of influence in the organization
All of this can be done using data you already have, but might not be exploiting it to the benefit of your organization– and the benefit of your taxpayers who consider THEIR protection to be YOUR job. A short demonstration of SAS Visual Investigator for Insider Threat can be accessed here.
